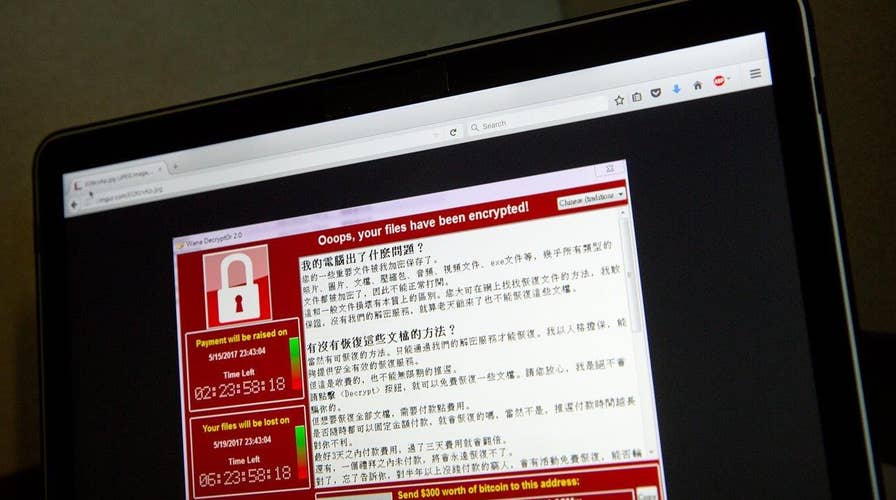
Global ransomware attack may be bigger than hackers intended
Tech Take: Alex Hamerstone and Malcolm Harkins share insight into the massive WannaCry ransomware attack that infected computers worldwide
Wanna cry? Blame Pyongyang.
It is “highly likely” that the WannaCry cybersecurity attack that infected more than 300,000 computers across the world this month was the handiwork of a hacking group linked to North Korea, Symantec Corp, the Silicon Valley-based cybersecurity firm, wrote in a blog post on Monday.
The hackers appear to be from the group known as Lazarus, which is known to have direct ties to the North Korean government. Symantec found multiple instances of code in WannaCry that Lazarus has used in the past, including in its 2014 attack on Sony Pictures Entertainment. The U.S. has accused North Korea of being behind the Sony attack.
Symantec listed numerous links between Lazarus and software the WannaCry hackers left behind in a less virulent version of the malware in February, including software used to wipe disks in the Sony attack.
CAN ARTIFICIAL INTELLIGENCE HELP THWART RANSOMWARE?
"Our confidence is very high that this is the work of people associated with the Lazarus Group, because they had to have source code access," Vikram Thakur, Symantec's security response technical director, told Reuters.
But he said it was unlikely that the hackers were working for North Korea this time. The operation was undisciplined, suggesting that the hackers may have been moonlighting or working as contractors.
"The intelligence community will probably take away from this that there is a possibility of splinters in the Lazarus Group, or members who are interested in filling their own pockets, and that could help," Thakur said.
WannaCry used a flaw in Microsoft's Windows operating system and a program the U.S. National Security Agency developed to take advantage of it. The malware surfaced on May 12 and disrupted hospitals, banks and schools throughout the world.
North Korea on Monday dismissed earlier accusations that it was behind WannaCry, calling them “a dirty and despicable smear campaign.”